“Single Sign-On (SSO): Your Key to Seamless and Secure Access
Artikel Terkait Single Sign-On (SSO): Your Key to Seamless and Secure Access
- Diving Deep Into IOS Development: A Comprehensive Guide
- The Undervalued Hero: Why Tech Documentation Is Critical And How To Master It
- The Rise Of The Intelligent Assistant: Navigating The World With AI By Your Side
- Embedded Systems: The Unseen Intelligence Powering Our World
- Navigating The Ethical Labyrinth: AI Governance In The 21st Century
Table of Content
Video tentang Single Sign-On (SSO): Your Key to Seamless and Secure Access
Single Sign-On (SSO): Your Key to Seamless and Secure Access
In today’s digital landscape, where users juggle numerous applications and services daily, the need for a streamlined and secure authentication process has never been greater. Enter Single Sign-On (SSO), a user authentication method that allows users to access multiple applications and websites with a single set of credentials. SSO eliminates the frustration of remembering numerous usernames and passwords while enhancing security and improving user experience.
This article delves into the intricacies of SSO, exploring its benefits, architecture, implementation methods, security considerations, and potential challenges.
What is Single Sign-On (SSO)?
At its core, SSO is a user authentication scheme that enables users to access multiple related, yet independent, software systems with a single ID and password. Instead of logging into each application individually, users authenticate once against a central identity provider (IdP). Once authenticated, the IdP verifies the user’s identity to the other applications (service providers or SPs) without requiring them to re-enter their credentials.
Think of it like using your hotel key card. You use it once to access your room, and then you can use it to access the gym, the pool, and other facilities within the hotel without having to re-register at each location. SSO functions similarly, providing a single point of authentication for multiple applications.
Benefits of Implementing SSO:
Implementing SSO offers a multitude of benefits for both organizations and end-users:
- Improved User Experience: The most immediate benefit is the elimination of password fatigue. Users no longer need to remember multiple usernames and passwords, leading to a more seamless and convenient experience. This translates to increased user satisfaction and productivity.
- Enhanced Security: SSO can significantly improve security by centralizing authentication and reducing the attack surface. By implementing strong authentication methods at the IdP, such as multi-factor authentication (MFA), organizations can protect against unauthorized access across all connected applications.
- Reduced IT Support Costs: Password resets are a significant drain on IT resources. SSO reduces the number of password-related issues, freeing up IT staff to focus on more critical tasks.
- Increased Productivity: Users spend less time logging in and out of applications, allowing them to focus on their work. This leads to increased productivity and efficiency.
- Simplified Access Management: SSO centralizes user access management, making it easier to onboard and offboard employees. Administrators can manage user access to multiple applications from a single location.
- Improved Compliance: SSO can help organizations comply with industry regulations and security standards by providing a centralized and auditable authentication system.
- Streamlined Integration: SSO simplifies the integration of new applications into the existing IT infrastructure by providing a standardized authentication mechanism.
- Enhanced Security Auditing: By centralizing authentication, SSO provides a single point for security auditing and monitoring, making it easier to detect and respond to security threats.
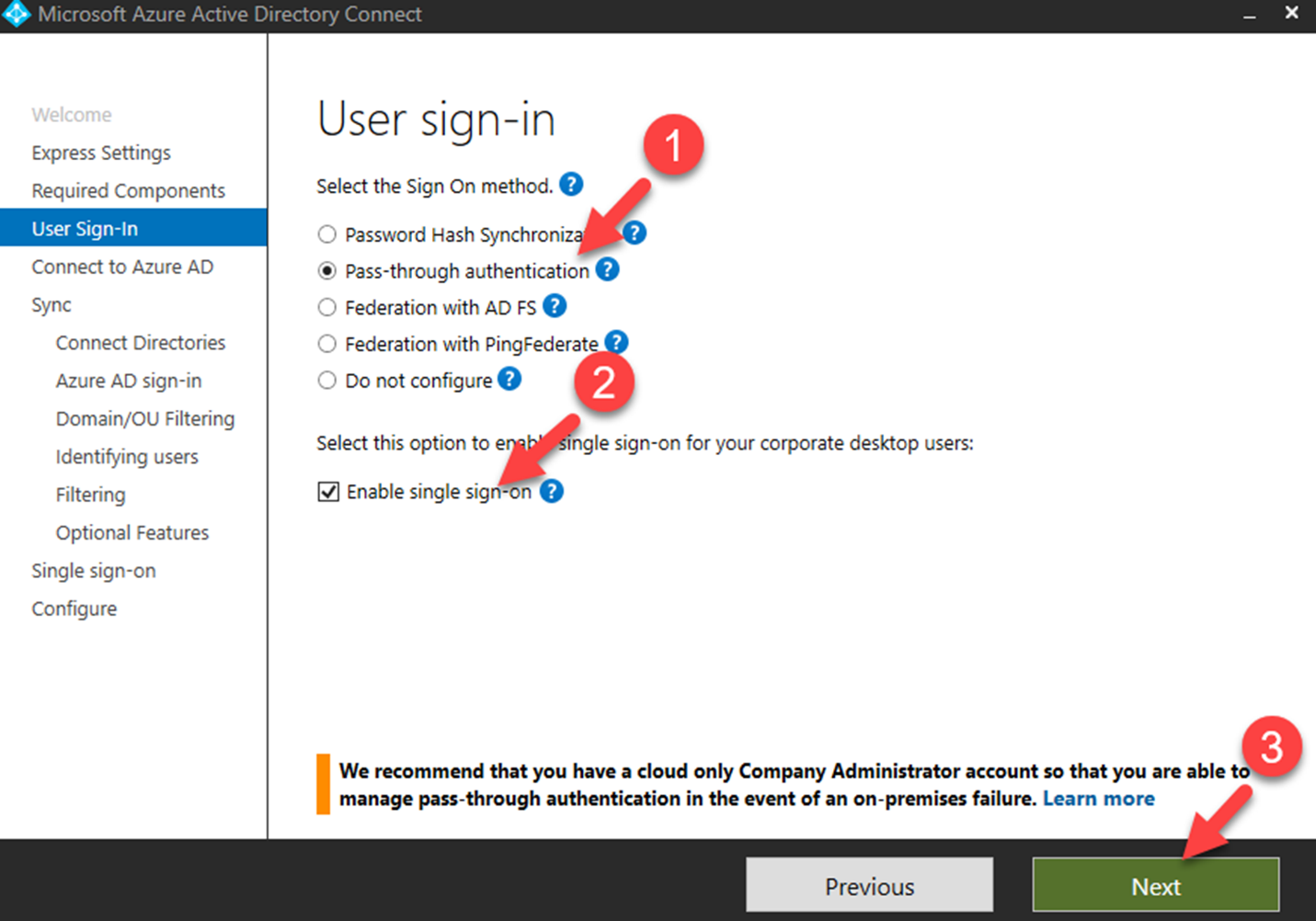
How SSO Works: A High-Level Overview
The SSO process typically involves the following steps:
- User Request: The user attempts to access a service provider (SP) application.
- Redirection to IdP: The SP determines that the user is not authenticated and redirects the user to the identity provider (IdP) for authentication.
- Authentication at IdP: The user authenticates at the IdP using their credentials (username and password, MFA, etc.).
- Authentication Assertion: The IdP verifies the user’s identity and generates an authentication assertion (a digital statement confirming the user’s identity).
- Redirection to SP with Assertion: The IdP redirects the user back to the SP, including the authentication assertion.
- Verification of Assertion: The SP verifies the authenticity and validity of the assertion with the IdP.
- Access Granted: If the assertion is valid, the SP grants the user access to the application.
This entire process happens seamlessly in the background, allowing the user to access the application without having to re-enter their credentials.
Key Components of an SSO System:
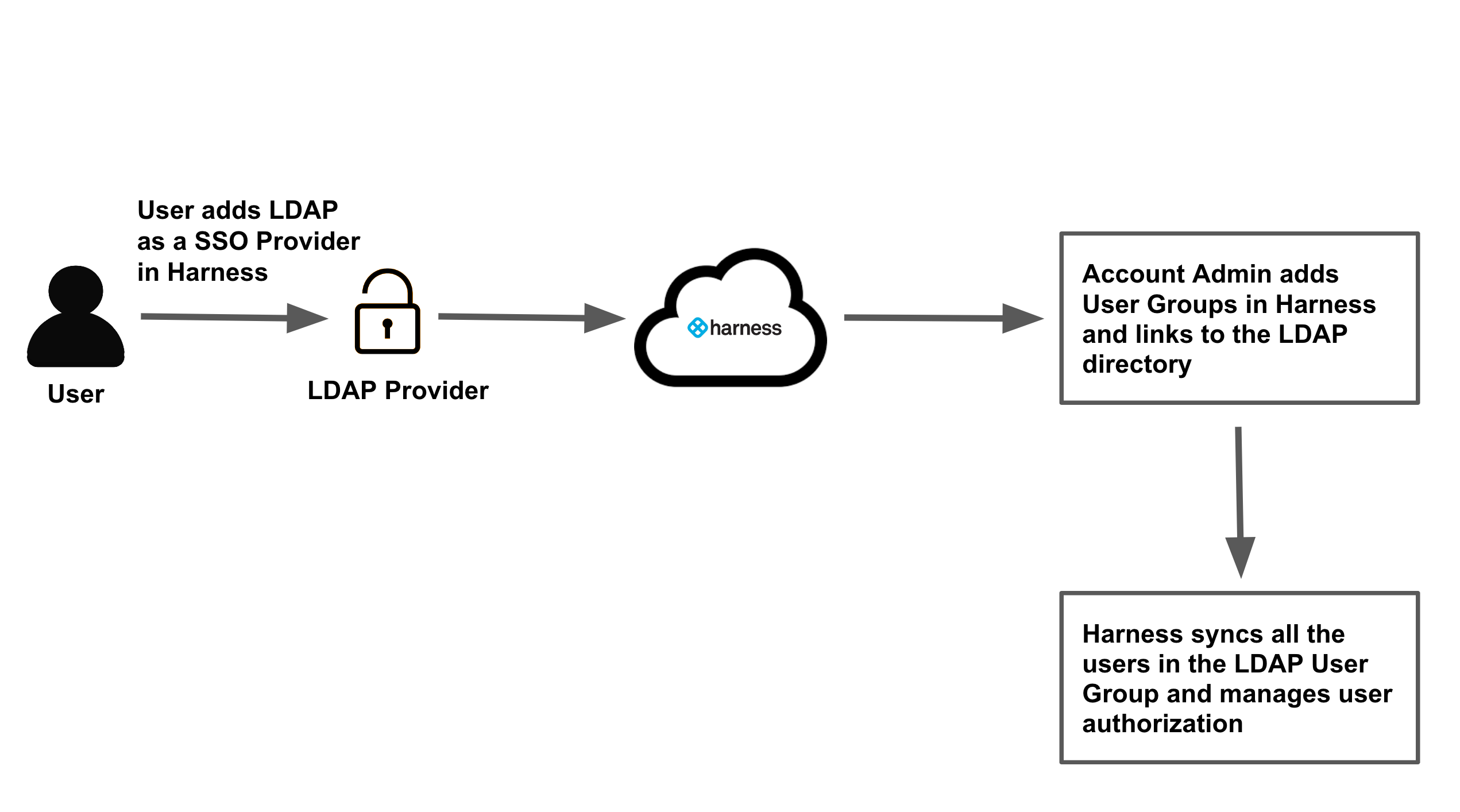
- Identity Provider (IdP): The IdP is the central authority responsible for authenticating users and providing information about their identity. It stores user credentials and manages authentication policies.
- Service Provider (SP): The SP is the application or website that users are trying to access. It relies on the IdP to authenticate users and authorize access.
- Authentication Protocol: The authentication protocol is the standard used for communication between the IdP and the SP. Common protocols include SAML, OAuth, and OpenID Connect.
- User Directory: The user directory is a repository of user information, such as usernames, passwords, and roles. It can be an internal directory like Active Directory or a cloud-based directory service.
Common SSO Protocols:
Several protocols are used to implement SSO, each with its own strengths and weaknesses. The most common protocols include:
- SAML (Security Assertion Markup Language): SAML is an XML-based open standard for exchanging authentication and authorization data between security domains. It is widely used in enterprise environments due to its security and flexibility.
- OAuth (Open Authorization): OAuth is an open standard for token-based authorization. It allows users to grant third-party applications access to their resources without sharing their credentials. OAuth is commonly used for social login and API authorization.
- OpenID Connect (OIDC): OpenID Connect is an authentication layer built on top of OAuth 2.0. It provides a standardized way for applications to verify the identity of users and obtain basic profile information. OIDC is becoming increasingly popular due to its simplicity and interoperability.
- Kerberos: Kerberos is a network authentication protocol that uses secret-key cryptography to authenticate users. It is commonly used in Windows environments.
The choice of protocol depends on the specific requirements of the organization and the applications being integrated.
Implementing SSO: Key Considerations:
Implementing SSO is a complex undertaking that requires careful planning and execution. Here are some key considerations:
- Choose the Right Protocol: Select the protocol that best meets the organization’s security requirements and integration needs.
- Select an IdP: Choose an IdP that is reliable, secure, and scalable. Options include on-premise solutions like Active Directory Federation Services (ADFS) and cloud-based solutions like Azure Active Directory and Okta.
- Integrate Applications: Integrate each application with the IdP, ensuring that they can properly handle authentication assertions.
- Implement Strong Authentication: Enforce strong authentication methods, such as multi-factor authentication (MFA), to protect against unauthorized access.
- Establish Clear Policies: Define clear policies for user authentication, access control, and security auditing.
- Test Thoroughly: Thoroughly test the SSO implementation to ensure that it is working correctly and securely.
- Provide User Training: Provide users with training on how to use the SSO system.
- Monitor and Maintain: Continuously monitor the SSO system for security vulnerabilities and performance issues.
Security Considerations for SSO:
While SSO enhances security, it’s crucial to address potential vulnerabilities:
- Compromised IdP: The IdP is a critical component of the SSO system. If the IdP is compromised, all connected applications are at risk. Therefore, securing the IdP is paramount.
- Phishing Attacks: Attackers may attempt to phish users’ credentials to gain access to the IdP. Implement anti-phishing measures and educate users about phishing scams.
- Session Hijacking: Attackers may attempt to hijack users’ SSO sessions. Implement session management controls to prevent session hijacking.
- Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF): Protect against XSS and CSRF vulnerabilities in the IdP and SP applications.
- Weak Authentication: Avoid using weak authentication methods, such as single-factor authentication. Implement multi-factor authentication (MFA) for enhanced security.
- Improper Configuration: Improper configuration of the SSO system can lead to security vulnerabilities. Follow best practices for configuring the IdP and SP applications.
Potential Challenges of Implementing SSO:
While SSO offers numerous benefits, organizations may face certain challenges during implementation:
- Complexity: Implementing SSO can be complex, especially for organizations with a large number of applications and users.
- Cost: Implementing SSO can be expensive, especially if it requires purchasing new software or hardware.
- Integration Issues: Integrating legacy applications with SSO can be challenging, especially if they do not support standard authentication protocols.
- Vendor Lock-in: Choosing a proprietary SSO solution can lead to vendor lock-in, making it difficult to switch to a different solution in the future.
- Downtime: Implementing SSO may require downtime, which can disrupt business operations.
SSO in the Cloud:
Cloud-based SSO solutions are becoming increasingly popular due to their scalability, flexibility, and ease of deployment. Cloud SSO providers offer a variety of features, such as multi-factor authentication, access management, and identity governance.
Future of SSO:
The future of SSO is likely to be shaped by several trends, including:
- Increased Adoption of Passwordless Authentication: Passwordless authentication methods, such as biometric authentication and security keys, are becoming increasingly popular.
- Integration with Zero Trust Security: SSO is being integrated with zero trust security models to provide more granular access control.
- Use of Artificial Intelligence (AI): AI is being used to detect and prevent fraudulent SSO attempts.
FAQ:
Q: What is the difference between SSO and password management?
A: SSO provides a single point of authentication for multiple applications, while password management tools store and manage users’ passwords for different applications. SSO eliminates the need to remember multiple passwords, while password management tools simply make it easier to manage them.
Q: Is SSO more secure than using individual passwords for each application?
A: Yes, SSO can be more secure than using individual passwords, especially if it is implemented with strong authentication methods like multi-factor authentication.
Q: What are the different types of SSO?
A: There are several types of SSO, including web-based SSO, desktop SSO, and mobile SSO.
Q: How much does it cost to implement SSO?
A: The cost of implementing SSO varies depending on the complexity of the implementation and the choice of IdP and SP solutions.
Q: What are some popular SSO providers?
A: Some popular SSO providers include Azure Active Directory, Okta, Ping Identity, and OneLogin.
Q: Can I implement SSO for my personal use?
A: Yes, you can implement SSO for your personal use using password managers with SSO features or by setting up your own IdP.
Q: What is MFA and how does it relate to SSO?
A: MFA (Multi-Factor Authentication) adds an extra layer of security to the authentication process. It requires users to provide two or more verification factors (e.g., password + code from a mobile app). When used with SSO, it strengthens the entire authentication chain, making it significantly harder for attackers to gain unauthorized access.
Conclusion:
Single Sign-On (SSO) is a powerful authentication method that offers numerous benefits for both organizations and end-users. By centralizing authentication and streamlining access management, SSO improves user experience, enhances security, reduces IT support costs, and increases productivity. While implementing SSO can be complex, the benefits far outweigh the challenges. As the digital landscape continues to evolve, SSO will remain a critical component of a secure and efficient IT infrastructure. By carefully planning and executing the implementation, organizations can leverage the power of SSO to create a seamless and secure access experience for their users.
